What Is a Zero-Day Attack?
“A zero-day exploit is as scary as it sounds: a problem so serious that developers have zero days to fix the error before it becomes an urgent issue.”
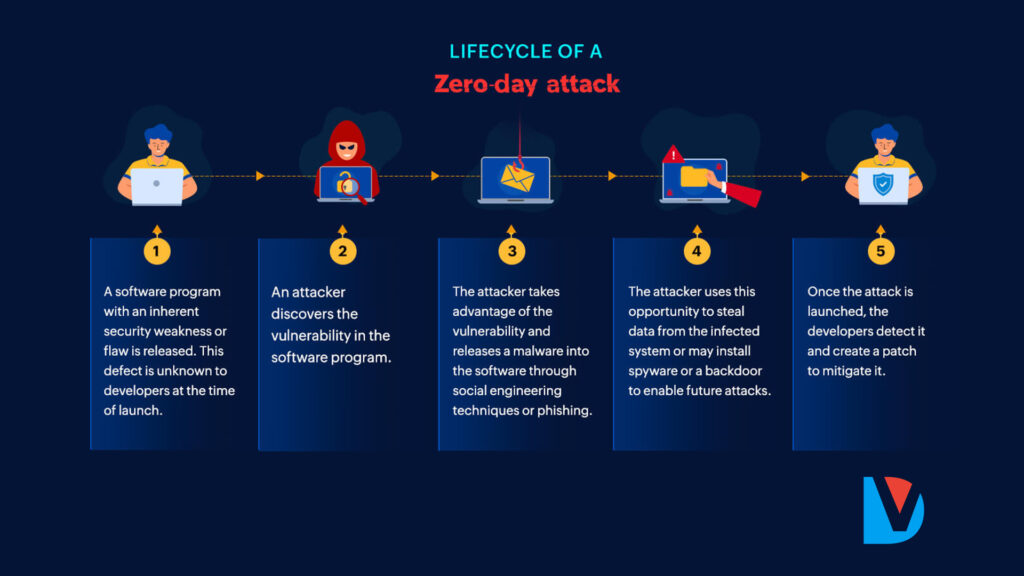
A zero-day attack, often referred to as a zero-day exploit, is a type of cyberattack that takes advantage of a software vulnerability or security flaw that is unknown to the software vendor or the public. In other words, it occurs on “day zero” of the discovery of the vulnerability, before anyone has had a chance to develop and distribute a fix or patch to address it.
Here are the key characteristics of a zero-day attack:
Unknown Vulnerability: Zero-day attacks target software vulnerabilities that have not been disclosed or are not yet publicly known. This means that software vendors are unaware of the issue, and there is no official fix available.
Limited Defense: Since there is no known fix for the vulnerability, there is often no effective defense against zero-day attacks when they occur. Traditional security measures like antivirus software and intrusion detection systems may not detect or prevent such attacks.
Rapid Exploitation: Zero-day vulnerabilities are valuable to attackers because they provide a window of opportunity to exploit a target system before anyone can mount a defense. Cybercriminals and state-sponsored hackers often use these exploits for their benefit.
High Impact: Zero-day attacks can have severe consequences, as they can compromise systems, steal sensitive data, or disrupt critical infrastructure without any prior warning.
Responsible Disclosure: When security researchers or ethical hackers discover a zero-day vulnerability, they typically follow a responsible disclosure process. This involves notifying the software vendor to allow them time to develop and release a patch before the vulnerability is publicly disclosed. However, not all discoveries follow this process, and some may be exploited before the vendor can respond.
To defend against zero-day attacks, organizations should adopt best practices for cybersecurity, such as regularly updating software and systems, using intrusion detection systems, employing network segmentation, and staying informed about emerging threats. Additionally, security researchers play a crucial role in identifying and reporting zero-day vulnerabilities so that vendors can issue patches and protect users from potential exploits.
Example:
The 2021 Google Chrome Hack
In April 2021, Google released an update for its Google Chrome browser on Windows, Linux, and Mac devices. Among other things, this update fixed a zero-day vulnerability that a hacker exploited. They called the vulnerability “CVE-2021-21224.”
The 2020 Zoom Hack
In July 2020, cybersecurity company 0patch reported that an anonymous person had identified a zero-day vulnerability in Zoom. The vulnerability allowed a hacker to run code remotely in Zoom once they gained entry by getting a user to click a link or open malware. The vulnerability only existed on computers running Windows 7 or earlier versions of Windows.
To prevent zero days attack, you can use Deverra soc service.
https://deverra.me/managed-detection-and-response-soc/
https://deverra.me/advanced-penetration-testing/
Read in LinkedIn: Click Here